Don't be a Victim in the Cloud - Cloud Service Concerns
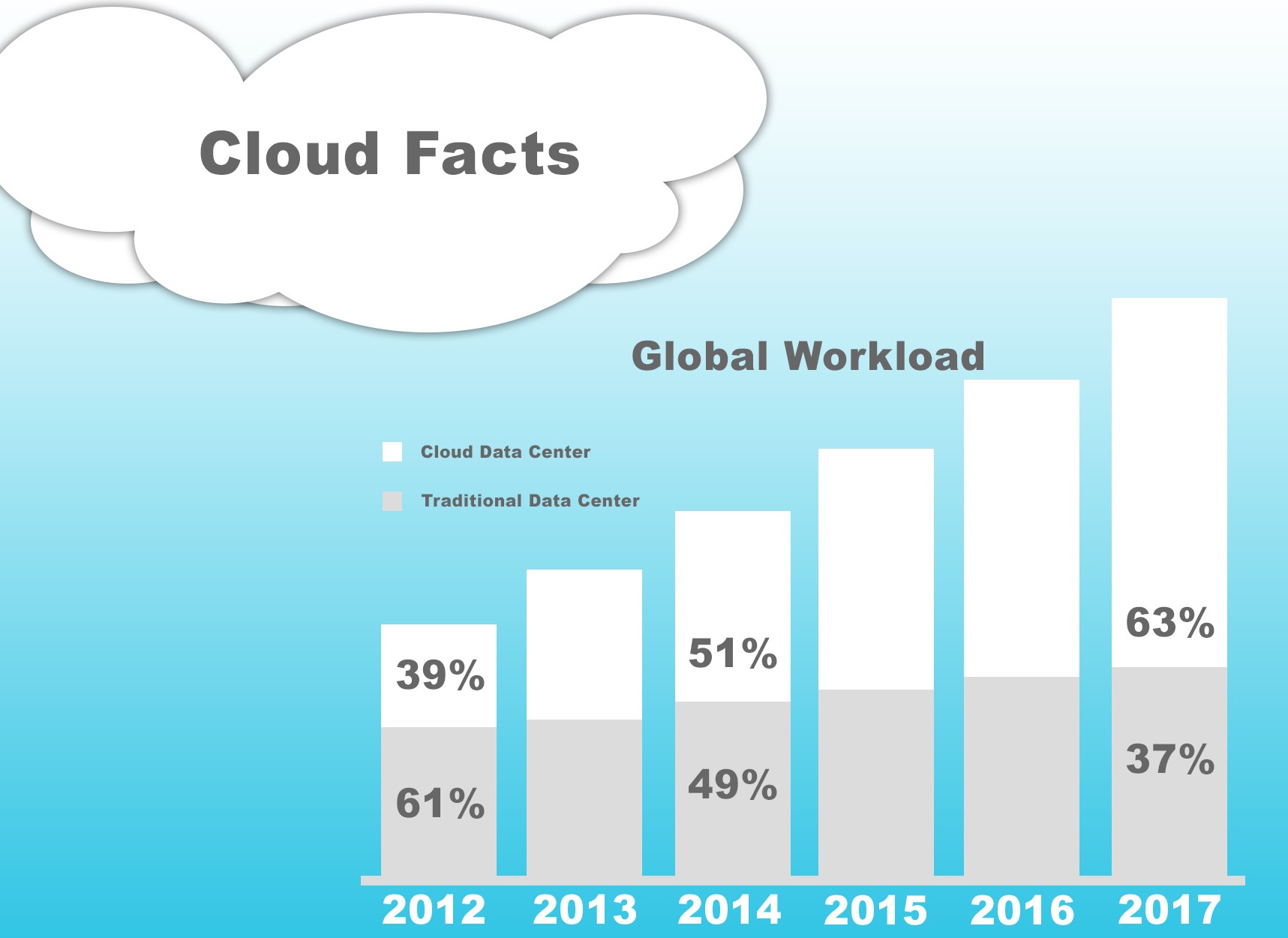
The cloud reshaped the landscape of IT. Companies no longer must face as many pure IT related impediments to
achieving their business goals. Companies today enjoy a lower barrier of entry and can compete more effectively thanks to the efficiency gains provided by the cloud. They no longer need to become experts in a litany of technical areas and manage all of it themselves.
For instance, it is no longer strictly necessary for a company to maintain their own datacenter or data warehouse. Instead this can be taken care of by a third party cloud provider who is responsible for all matters of maintenance and security of their clients sensitive information and processes. All the costs associated with the in-house development and upkeep of such facilities can now be allotted to initiatives more directly in keeping with achieving business goals.
Further, thanks to its virtualized nature, the cloud is innately scalable and flexible. This means that, in a manner invisible to the client, resources can be allotted in proportion to the demand of the task dynamically.
For all the benefits of the cloud, there are still some legitimate concerns one should be aware of. In particular is the issue of security.
- Internal Controls - While cloud providers offer many security measures, the impetus is still on the company itself to properly utilize and tie them in to internal methods of control. Legacy methodologies may no longer be applicable. No matter how familiar and vetted they are internally, there should be a complete reassessment of security tools and protocols in relation to the cloud.
- Local Security - User access controls, network security, data encryption, application security, and physical security measures are still paramount for the client end of the relationship. The client itself is still completely responsible for all data delivered to and accepted from the cloud provider. A compromise on the local end may very well result in a breach of the cloud itself, and rendering one's processes and data vulnerable.
A chain is only as strong as its weakest link.
Still, there is the risk of the cloud service provider itself being compromised completely externally. This is an eventuality that a company should realize as completely possible, if however unlikely, when leveraging cloud services.
So What?
Ultimately, not being a victim in the cloud entails the very same level of commitment to due diligence that behooves every business. It simply requires an understanding that the cloud presents a different set of challenges and a willingness to change in order to address them.


